Is Your AV Deployment Secure?
The need for security impacts everyone. And, unfortunately, unmonitored access points can quickly lead to a costly data breach. The massive Target breach from a few years ago was the result of an unprotected accesses point provided to an HVAC contractor. Similar attacks have happened through improperly secured fish tanks, POS units or even reward-centric credential systems.
This is increasingly important in the current experience economy where content and data combine to provide users, customers and guests with the highly customized type of experiences they expect. Oftentimes these experiences flow through audiovisual and communication (AVC) equipment. These customers and guests are trusting organizations with information in exchange for an enhanced experience. In this equation, the impetus is understandably on the organization to protect that data.
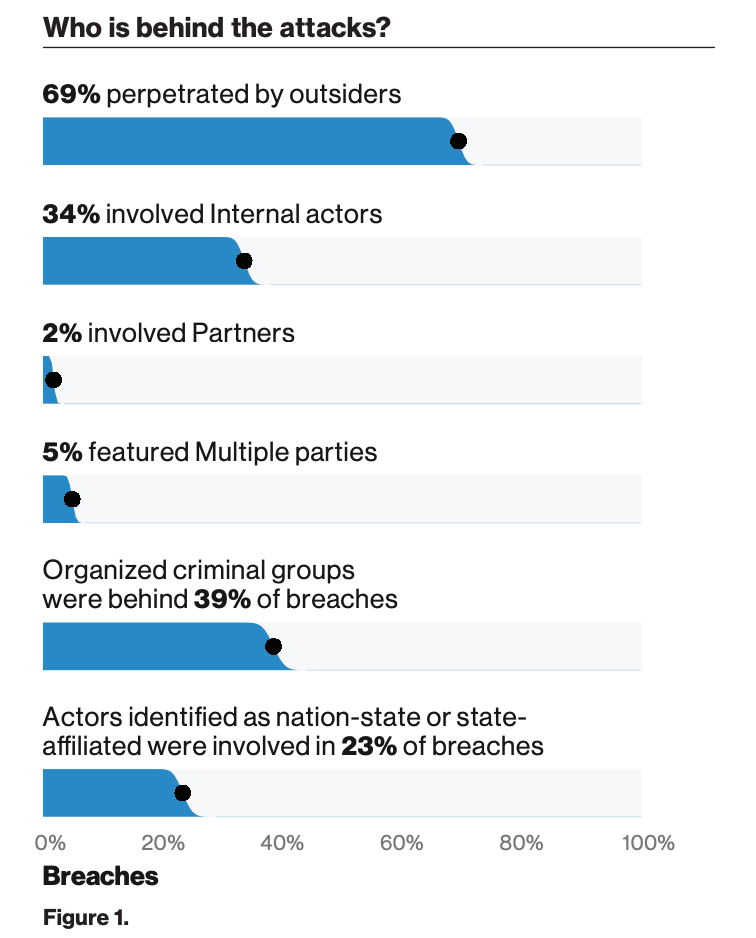
Image from Verizon 2019 Data Breach Investigations Report.
As the Verizon 2019 Data Breach Investigations Report point out, no one is immune to attacks in today’s evolving threat landscape. “No organization is too large or too small to fall victim to a data breach. No industry vertical is immune to attack. Regardless of the type or amount of your organization’s data, there is someone out there who is trying to steal it. Having a sound understanding of the threats you and your peer organizations face, how they have evolved over time, and which tactics are most likely to be utilized can prepare you to manage these risks more effectively and efficiently.”
Best Practices for Keeping Your AVC Technology Out of the Mix
Security Hygiene and Integrity. For today’s interactive systems to function properly and deliver a customized experience, it usually requires a seamless connection to any number of information and media data bases. Remember to always keep the protection active in these systems and apply patches as they become available. The lack of attention to detail can undoubtedly create open doors for today’s advanced hackers to make their way into all of your systems.
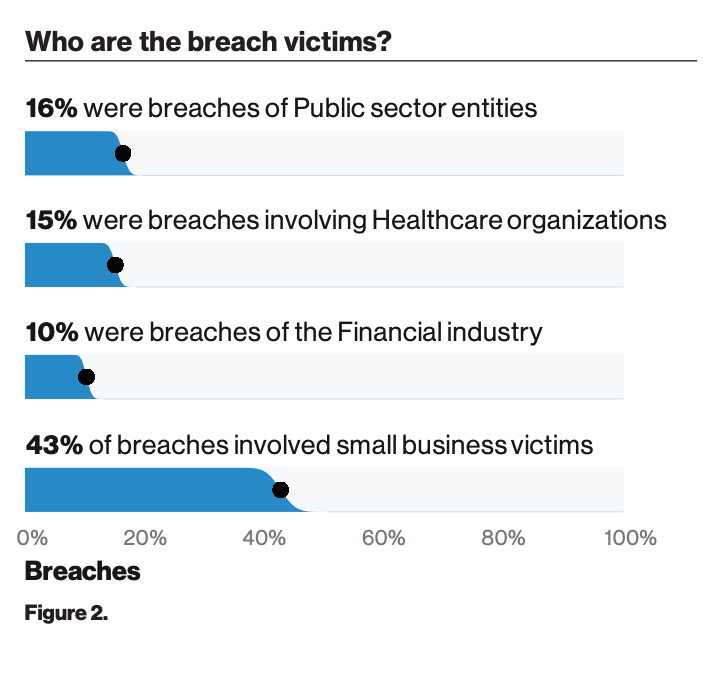
Image from Verizon 2019 Data Breach Investigations Report.
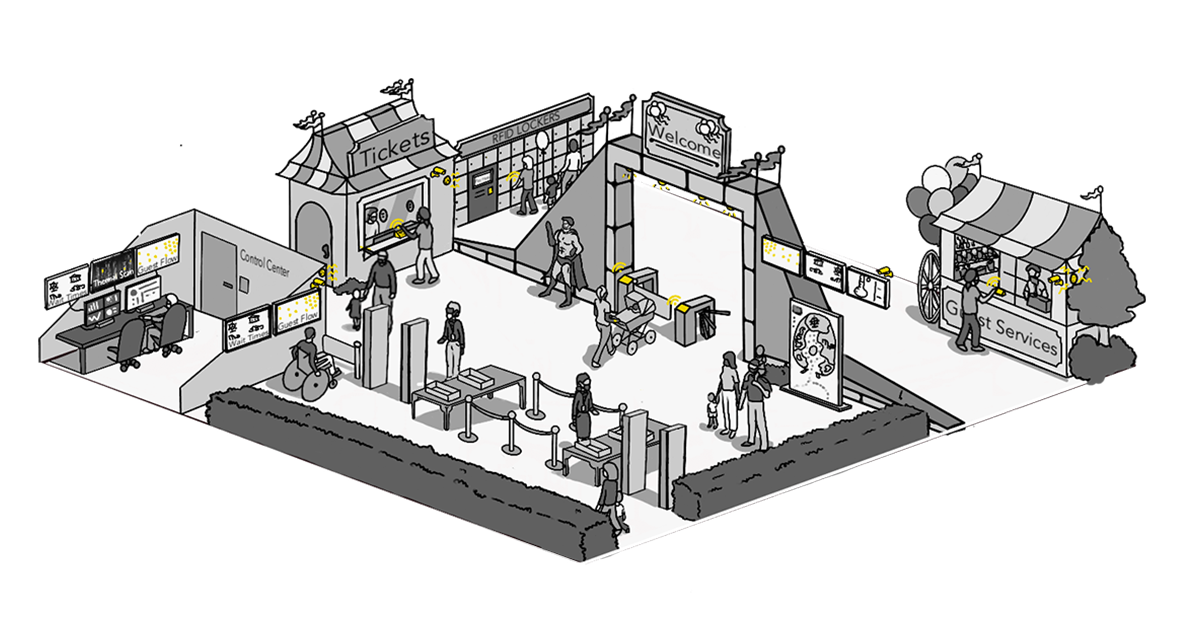
Monitor Your People and Partners. Track insider behavior by monitoring and logging access to sensitive data. The right partners can be true assets because they understand the technology deployments and how to protect them. However, not everyone needs unmonitored access. Likewise, there is no reason why every access point (such as a wayfinding display) needs to authorization to access the entire data network. Pay close attention to fraudulent transactions or anything that appears to be outside the norm.
Manage Credentials. As RFID becomes the norm, it allows you to provide new experiences. It also helps with security. Use these credentials as tools to limit where people can access. RFID can also play a role in monitoring activity to ensure that people including customers or guests cannot gain access to data that isn’t relevant to them. This can also help identify when a bad actor has gained access to staff credentials. According to the report, “Social attacks are effective ways to capture credentials. Monitor email for links and executables. Give your teams ways to report potential phishing or pretexting.”
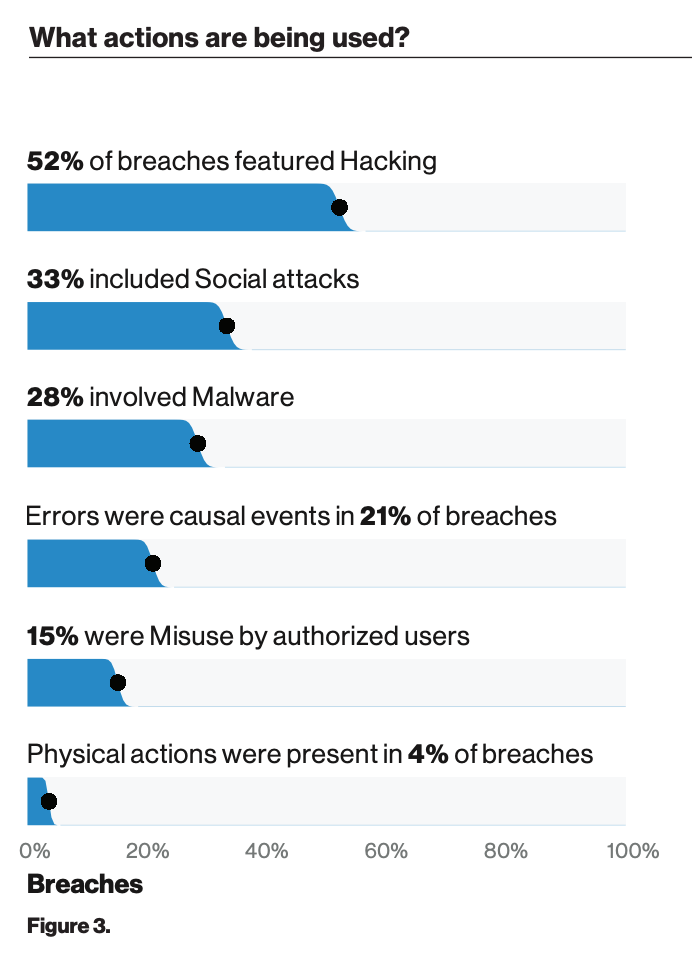
Image from Verizon 2019 Data Breach Investigations Report.
Need help ensuring that your AV deployment remains secure? Having an experienced partner like Electrosonic on your side can prove instrumental. With 55+ years of practical experience finding effective uses for technology, Electrosonic understands not only the importance of security, but also how to ensure your system meets expectations. Click here to learn more.
Yiannis Cabolis
Yiannis Cabolis, Director of Technology Innovation at Electrosonic, shares the inside track on how technology drives innovation. He brings 30 years’ experience monitoring emerging technologies, developing best practices and driving Research and Development to solve challenges and help clients understand how to benefit from the latest engineered technology solutions.










.jpg?width=1500&height=995&name=ELC501_N17_medium%20(1).jpg)